Study Guide
Field 068: Computer Science
Sample Multiple-Choice Questions
Domain I—Data and Analysis
Objective 0001
Understand the collection, analysis, evaluation, and interpretation of data.
1. A student has been assigned a research project for a history class. Prior to conducting research, the student should take which of the following steps first?
- identifying the resources that will be needed
- creating an outline of the major ideas to address
- formulating a well-defined research question
- deciding how the information in the report will be presented
- Answer
-
Correct Response: C.
A well-defined research question provides focus and purpose for a research project. It acts as a guide that must be kept in mind during all subsequent steps. Therefore, it must be the first step in any research project.
Objective 0002
Understand the representation and presentation of data.
2. A digital audio recording application takes 44,100 samples of a sound per second for a single track of music. If each sample is 16 bits, which expression represents the size of a digital file in bytes containing a single track of one minute of music?
- 44,100 times 60 all over 8 times 16 bytes
- 44,100 times, open paren, 16 plus 60, close paren, times 8 bytes
- 44,100 times 16 times 60 all over 8 bytes
- 44,100 times 16 times 60 times 8 bytes
- Answer
-
Correct Response: C.
There are 44,100 samples in one second, 16 bits in one sample, 1 byte in 8 bits, and 60 seconds in one minute. Therefore, the number of bytes in one minute of music can be calculated as:
44,100 samples per 1 second times 16 bits per 1 sample times 1 byte per 8 bits times 60 seconds per 1 minute times 1 minute over 1 equals 44,100 times 16 times 60 all divided by 8. The units are bytes. The units cancel leaving only bytes as a unit.
Objective 0003
Understand the storage, management, and manipulation of data.
3. Which of the following strategies would be most effective for preventing a breach in data security due to a phishing attack?
- training employees on how to recognize suspicious e-mails
- scanning all e-mail attachments for viruses
- requiring employees to regularly change their passwords
- updating firewall and database access settings
- Answer
-
Correct Response: A.
Phishing is a specific type of cybercrime in which victims are contacted and tricked into disclosing personal identification or other confidential information. This is typically done through e-mail. Phishing attacks involving sending information that appears to come from a legitimate source, such as a bank or the government to the potential victim. To protect against phishing in an organization, employees must be trained to recognize it.
Domain II—Computing Devices and Networks
Objective 0004
Understand computing devices, their components, and basic troubleshooting strategies.
4. The ability for smart home systems such as heating, air conditioning, and lighting to communicate with one another and to be operated remotely is made possible by the combination of Wi-Fi connections and which of the following additional technologies?
- LEDs
- robotics
- solid-state memory
- microsensors
- Answer
-
Correct Response: D.
A microsensor is an integrated device containing sensing equipment, a microprocessor, memory, and a radio transmitter/receiver. These devices gather information, such as temperature, lightning levels, and electricity use. The information about the conditions in a smart home is communicated to various control systems and remote users. The data can then be analyzed and appropriate actions taken, such as lowering the temperature of the home or increasing the lighting level.
Objective 0005
Understand networks and the Internet.
5. A student is developing a Web page. The student would most likely use a client-side scripting language for which of the following purposes?
- adding interactive features to the Web page
- creating the visual design, layout, and style of the page
- storing information input by the user in a remote database
- converting a file written using a word processor to a Web page
- Answer
-
Correct Response: A.
Client-side scripting is used to write computer programs (scripts) that are executed by the web browser. Client-side scripting provides two major advantages over server-side scripting. The first is that the Web page can respond very quickly to the user's actions since no data needs to be sent to the server and back to the client (the browser). The second is that the server is not burdened with processing multiple requests from multiple users. Modern Web pages are expected to include interactive interfaces that react almost instantaneously to user actions. Large numbers of users of such modern interactive Web pages can overload servers and create a frustratingly slow user experience if they did not use client-side scripting.
Objective 0006
Understand concepts related to digital tools, resources, and design principles.
6. Use the spreadsheet table below to answer the question that follows.
| blank | A | B | C | D |
|---|---|---|---|---|
| 1 | Day | Computers Repaired | Time Required (Hours) | Average Number of Computers Repaired per Hour |
| 2 | Monday | 23 | 12 | 1.92 |
| 3 | Tuesday | 0 | 0 | #DIV/0! |
| 4 | Wednesday | 19 | 11 | 1.73 |
| 5 | Thursday | 24 | 13 | 1.85 |
A student is using a spreadsheet and wants to type "Not applicable" in column D when division by zero occurs. The student finds the following syntax for the appropriate command in a help file.
IF(Condition, True Result, False Result)
Which of the formulas could be entered in cell D3 to achieve this goal?
- =IF(B3 = 0, "Not Applicable", B3/C3)
- =IF(B3 = 0, B3/C3, "Not Applicable")
- =IF(C3 = 0, "Not Applicable", B3/C3)
- =IF(C3 = 0, B3/C3, "Not Applicable")
- Answer
-
Correct Response: C.
The "Average Number of Computers Repaired per Hour" in column D is calculated by dividing the number of "Computers Repaired" in column B by the "Time Required (Hours)" in column C. In order to test if division by zero occurs, the "Condition" to be tested for is if the value in column C is equal to zero. For row 3, the "Condition" would be "C3 = 0". If the "Condition" is true, then the "True Result" should be "Not Applicable". If the "Condition" is false, then the calculation should be performed, and hence the "False Result" is B3/C3 for row 3. Therefore, the formula to be entered into cell D3 should be the following:=IF(C3 = 0, "Not Applicable", B3/C3)
Domain III—Algorithms
Objective 0007
Understand concepts and processes related to problem solving and algorithm development.
7. Use the information below to answer the question that follows.
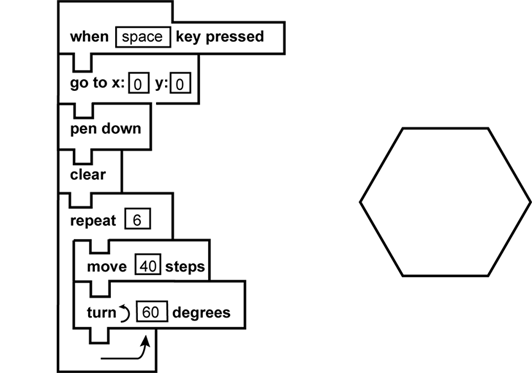
The graphic shows code expressed in a block-based computer language on the left and a regular hexagon (six-sided figure with all sides and angles equal in measure) on the right. The top block says "when space key pressed". The next block says "go to x = 0 and y = 0". The third block says "pen down". The fourth block says "clear". The fifth block says "repeat 6". The next two blocks are indented to the right. The sixth block says "move 40 steps". The seventh block says "turn left 60 degrees." The final block has an arrow indicating that control should go the repeat block.
A student uses block-based programming language to draw the geometric figure shown on the right. Which of the following aspects of algorithm design is best demonstrated by this programming code?
- sequence
- iteration
- selection
- recursion
- Answer
-
Correct Response: B.
The algorithm uses a loop to repeat a small set of instructions six times. When the space bar is pressed, the drawing pen goes to the origin, the pen is put down to draw, and any content already on the screen is cleared. Then the program is told to repeat the next two indented blocks 6 times (move forward 40 steps, turn [left] 60 degrees). The next block indicates the program should return to first indented block under the repeat block. This is an example of using iteration to avoid having to write out identical sets of instructions multiple times.
Objective 0008
Understand concepts and processes related to the use of algorithms.
8. Use the information below to answer the question that follows.
print("How many total grades do you have?")
num = userInput() //gets input from the user
if (num = 0)
print("You have to have at least one grade!")
exit() //exits the program
i = num
grade = 0.0
sum = 0.0
//algorithm
A program prompts the user for a total number of grades, and then asks the user to enter the grades, one at a time. Given the information above, which algorithm could be used to find the average grade?
-
while ( i is greater than 0)
print("Input one grade and hit enter.")
grade = userInput()
sum = grade
i = i - 1
print(sum/num) -
while ( i is greater than 0)
print("Input one grade and hit enter.")
grade = userInput()
sum = i + grade
i = i - 1
print(sum/num) -
while ( i is greater than 0)
print("Input one grade and hit enter.")
grade = userInput()
sum = num + grade
i = i - 1
print(sum/num) -
while ( i is greater than 0)
print("Input one grade and hit enter.")
grade = userInput()
sum = sum + grade
i = i - 1
print(sum/num)
- Answer
-
Correct Response: D.
The program first asks for the user to input the number of grades. This must be a non-zero value. The variable num represents the number of grades, and the variable sum is set to zero. The value of i in the while loop is also set to num. With each execution of the while loop, grade is given the value of the user input, and sum is increased by the value of grade so that sum is the cumulative total of all of the grade entries thus far. This increasing of sum is carried out by the statement: sum = sum + grade. Finally, the average grade is calculated by dividing the cumulate total, sum, by the number of grades, num, and the result is printed to the screen.
Objective 0009
Understand concepts and processes related to computer science and program design and development.
9. Use the algorithm below to answer the question that follows.
//math.intRandom(a, b) generates a random integer between a //(inclusive) and b (inclusive)
print "Click the button to display a random number."
//code for button
button = display button
button text = "Generate a random number between 1 and 6"
whenclicked = "myFunction()"
//code for function
myFunction()
print"math.intRandom(1,6)"
root.main()
This algorithm best demonstrates which of the following programming concepts?
- procedural
- event-driven
- object-oriented
- recursive
- Answer
-
Correct Response: B.
This is an example of an event-driven programming algorithm since the flow of the algorithm is determined by an event, in this case the clicking of a button, and not by the order of a sequence of commands. The response to the event is carried out by an event handler, in this case the function whenclicked.
Domain IV—Programming
Objective 0010
Understand concepts of programming.
10. Use the pseudocode below to answer the question that follows.
CLASS Character
string name
integer health
walk()
run()
jump()
Character(name, health)
MAIN
Character Char1 = ("Ranger", 10)
A student created the above class for a game. Which of the following is a proper way to invoke a method of CLASS Character?
- Ranger.name
- Ranger.run()
- Char1.health
- Char1.jump()
- Answer
-
Correct Response: D.
In this example, CLASS Character has class variables name and health and class methods walk(), run(), and jump(). An object called "Char 1" is constructed as an instance of CLASS Character. The syntax for invoking a method to be performed on an object is objectName.methodName(). In this case, objectName is Char 1, and methodName() could be walk(), run(), and jump(). Hence Char 1.jump() invokes the method jump().
Objective 0011
Understand data types and variables.
11. A student is developing a program that allows a user to create a personal budget. The program prompts the user to input their weekly earnings. Which of the following types of variable should be used for this data?
- float
- string
- integer
- Boolean
- Answer
-
Correct Response: A.
The float data type stores floating-point decimal numbers. Of the choices given, this is the most appropriate data type for variables that store decimal values, such as currency.
Objective 0012
Understand characteristics and uses of operators, conditional statements, and loops.
12. Use the pseudocode below to answer the question that follows.
x = 0
for (i = 2; i is less than or equal to 6; i = i + 2)
x = x + i
print(x)
What will this code print?
- 6
- 9
- 12
- 20
- Answer
-
Correct Response: C.
The loop in this pseudocode is executed for i = 2, 4, and 6 since i starts at 2 and is incremented by 2 while i is less than or equal to 6. The variable x has an initial value of 0 and is incremented by the value of i with each execution of the loop. The trace table shown below gives the values of i and x with each iteration.blank i x x + i initial 2 0 2 loop 1 4 2 6 loop 2 6 6 12 When the loop terminates, i = 6 and x = 12. Hence, the value, 12, will be printed.
Domain V—Impacts of Computing; Instruction and Assessment
Objective 0013
Understand digital citizenship and the responsible use of technology and information.
13. A computer user changes a setting in the browser to enable private browsing. Which of the following statements best describes the effect of this action?
- The use of cookies is disabled for all Web sites.
- The user's computer is assigned a dynamic IP address.
- Web sites visited by the user do not appear in the computer's browsing history.
- The user's computer is not detected by servers and other computers on the Internet.
- Answer
-
Correct Response: C.
Most web browsers include a private browsing option. While this option varies slightly between browsers, the principal common feature is that the computer's browsing history, while operating in private browsing mode, is not saved.
Objective 0014
Understand the social and global impacts of computer science and technology.
14. Deep learning algorithms require very large data sets in order to train a neural network algorithm how to make decisions. Which of the following best describes a significant social concern with the way that many algorithms based on artificial intelligence and deep learning are developed and perfected?
- The large data sets used to train the algorithms may contain biased information.
- The algorithms are generally proprietary and not available for public view.
- The data sets may contain information that is not particularly useful for learning.
- The algorithms may require too much time to generate an optimal solution.
- Answer
-
Correct Response: A.
Large data sets can contain racial, gender, ideological, and other biases. If the data used to train an AI (artificial intelligence) algorithm does not accurately represent the diversity of the contexts in which it will be deployed, its reliability may be compromised in real-world situations in a manner that could be biased and discriminatory. This is a serious concern given the high-stakes decisions that are made using AI.
Objective 0015
Understand effective instruction and assessment in computer science.
15. Use the information below to answer the question that follows.
Classroom Activity
- Fill eight identical paper cups with different amounts of sand and cover with lids.
- Mix up the cups so that the amount of sand in each container is unknown.
- Using a scale, order the cups from lightest to heaviest by comparing two at a time.
- Reflection: Was the approach you took the most effective way to order the containers two at a time? How did it work? Is there a better way to arrange the cups in order?
The instructional activity above is most appropriate for promoting learning related to which of the following elements of computational thinking?
- abstraction
- algorithm development
- decomposition
- pattern recognition
- Answer
-
Correct Response: B.
In this activity, students are asked to come up with a logical method for solving a problem. They then test the method to verify its effectiveness. Finally, they reflect upon whether there might be a better method to achieve the same goal. While following this sequence of steps, students are practicing the same computational-thinking processes that are carried out during algorithm development.
